![[Note]](/media/com_docimport/admonition/note.png) | Note |
|---|---|
|
This feature is only available in the Professional release |
![[Warning]](/media/com_docimport/admonition/warning.png) | Warning |
|---|---|
|
This feature is only available on servers running the Microsoft IIS web server. If your server is using Apache or NginX the button to launch this feature will not be shown. If the server type cannot be detected you will see this feature but you should consult with your host whether it will have any effect on your server. |
One of the most important aspects of managing a web site hosted on an IIS server is being able to fine-tune your site configuration file, web.config. This file is responsible for many web server level tweaks, such as enabling the use of search engine friendly (SEF) URLs, blocking access to system files which should not be accessible from the web, redirecting between pages based on custom criteria and even optimising the performance of your site. On the downside, learning how to tweak all those settings is akin to learning a foreign language. The tool of Admin Tools is designed to help you create the part of such a file used for security and performance optimisation by utilizing a point-and-click interface.
![[Tip]](/media/com_docimport/admonition/tip.png) | Tip |
|---|---|
|
If you ever want to revert to a "safe default", just set all of the options on this page to "Off" and click on "Save and create web.config". This will create a web.config file that's practically the same as the web.config.txt file shipped with Joomla! itself. |
![[Important]](/media/com_docimport/admonition/important.png) | Important |
|---|---|
|
This feature relies on Microsoft's URL Rewrite 2.0 module for Microsoft IIS. This is the same optional IIS module required by the web.config shipped with Joomla! to use SEF URLs without index.php in them. If you cannot use Joomla!'s web.config after renaming the web.config.txt file to web.config then you will NOT be able to use our web.config Maker feature. If this is the case please contact your host and ask them to install and enable the URL Rewrite 2.0 module for IIS. |
![[Warning]](/media/com_docimport/admonition/warning.png) | Warning |
|---|---|
|
This feature, like Joomla!'s SEF URLs, require IIS 7 or later. If you have an older version of IIS such as IIS 6 you will NOT be able to use this feature. Unfortunately IIS 6 and lower lack the necessary features to create a security tightening web.config file. |
The top part of the web.config maker page contains the standard toolbar buttons you'd expect:
The web.config Maker's toolbar
-
saves the changes you have made in this page's options without actually creating the customized
web.configfile. This should be used when you have not decided on some options yet, or if you want to preview the generatedweb.configfile before writing it to disk. -
is the logical next step to the previous button. It not only saves the changes you made, but also creates and writes the new
web.configfile to the disk. If you already had aweb.configfile on your site, it will be renamed toweb.config.admintoolsbefore the new file is written to disk. -
pops up a dialog where you can see how the generated
web.configfile will look like without writing it to disk. This dialog shows the saved configuration. If you have modified any settings they will not be reflected in there until you click either of the previous two buttons. -
The button takes you back to the Control Panel page.
Below the toolbar there are five panes with different options, described below. Before you do that, please read and understand the following warning. Support requests which indicate that you have not read it will be replied with a link back to this page.
Basic security
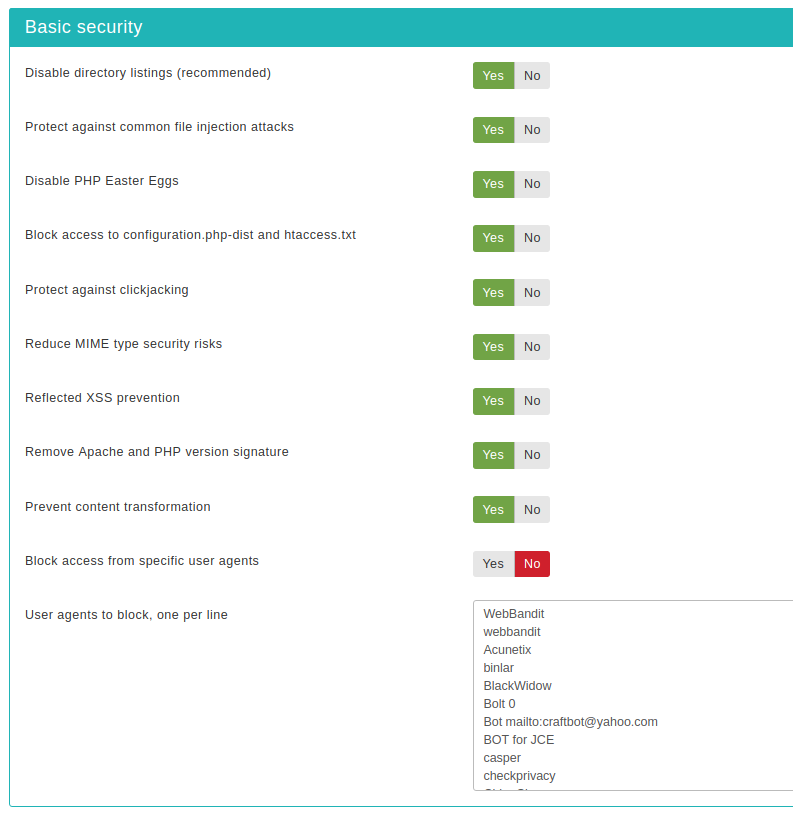
- Disable directory listings (recommended)
-
When disabled, your web server might list the files and subdirectories of any directory on your site if there is no index.html file inside it. This can pose a security risk, so you should always enable this option to avoid this from happening.
- Protect against common file injection attacks
-
Many attackers try to exploit vulnerable extensions on your site by tricking them into including malicious code hosted on the attacker's server. Enabling this option will protect your server against this kind of attacks. This works by preventing any URL which references an http:// or https:// URL in the query string. Sometimes these are legitimate requests. For example, some gallery components use them. In this case you are recommended to use the RFIShield (Remote File Inclusion protection) in the Web Application Firewall and turn this web.config Maker option OFF.
- Disable PHP Easter Eggs
-
PHP has a fun and annoying feature known as "Easter Eggs". By passing a special URL parameter, PHP will display a picture instead of the actual page requested. Whereas this is considered fun, it is also widely exploited by attackers to figure out the version of your PHP installation (these images change between different versions of PHP) and launch hacking attacks targeting your specific PHP version. By enabling this option you completely disable access to those Easter Eggs and make it even more difficult for attackers to figure out the details of your server.
Note: You are advised to also set
expose_phptoOffin yourphp.inifile to prevent accidental leaks of your PHP version. - Block access to configuration.php-dist and htaccess.txt
-
These two files are left behind after any Joomla! installation or upgrade and can be directly accessed from the web. They are used by attackers to tell the Joomla! version you are using, so that they can tailor an attack targeting your specific Joomla! version. Enabling this option will "hide" those files when accessed from the web (a 404 Not Found page is returned), tricking attackers into believing that these files do not exist and making it slightly more difficult for them to deduce information about your site. This option also hides the web.config.txt file included in Joomla! 3 and later for use with the IIS server.
- Protect against clickjacking
-
Turning on this option will protect you against clickjacking. It does so by preventing your site's pages to be loaded in a, Frame, IFrame or Object tag unless this comes from a page inside your own site. Please note that if your site relies on its pages being accessible through frames / iframes displayed on other sites (NOT on your site displaying content from other sites, that's irrelevant!) then you should not enable this option. If unsure, enable it.
- Block access from specific user agents
-
When enabled, it will block any site access attempt if the remote program sends one of the user agent strings in the User agents to block, one per line option. This feature is designed to protect your site against common bandwidth-hogging download bots and otherwise legitimate tools which are more usually used for hacking sites than their benign intended functionality.
- User agents to block, one per line
-
The user agent strings to block from accessing your site. You don't have to enter the whole UA string, just a part of it. The default setting includes several usual suspects. Separate multiple entries by a single newline character (that is a single press of the ENTER key). Do note that some server with mod_security or mod_evasive installed will throw an "Access forbidden" message if you try to save the configuration settings when this field contains the word "WGet". If you come across this issue it is not a bug with Admin Tools or Joomla!, it is a server-level protection feature kicking in. Just avoid including the word Wget and you should be out of harm's way.
- Block common exploits
-
Enabling this option will include a set of options recommended by Joomla! to protect against (obsolete) common exploits which no longer have any effect on Joomla! 2.5 and later. It's still a good idea to enable this option.